Too Many Tools, Too Little Time: Making Automation Work Across Silos
When I ask customers what’s holding them back from full certificate lifecycle automation, the answer isn’t always “budget” or “skills.” More often, it’s this: we have too many tools, too many teams, and no single way of working across them.
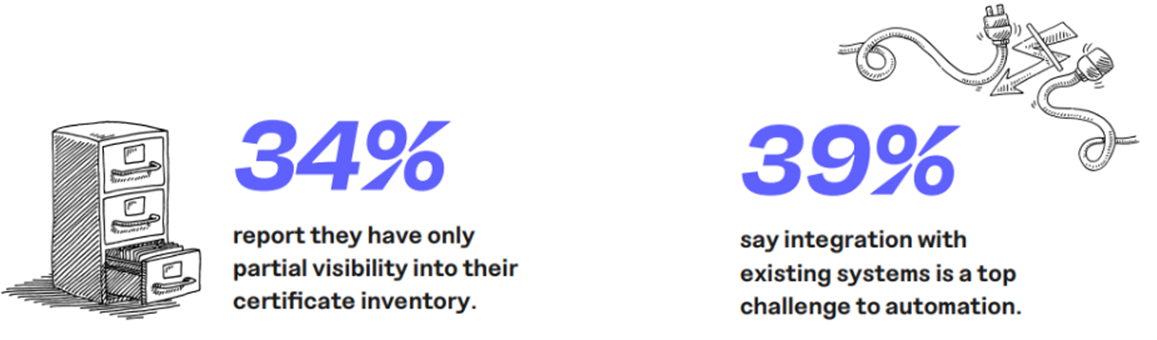
Managing digital certificates is harder than it should be — and most customer teams know it. A recent Keyfactor survey of 450 PKI and CLM practitioners backs this up: one in three practitioners admitted they can’t fully see or manage all their certificates. Even those who have automated key parts of the process still struggle with certificates hiding in unexpected places — like forgotten devices or third-party cloud apps. Integration hurdles only make the job tougher.
And that’s the real challenge: the problem isn’t just what to automate, it’s how to connect it all together.
The Silo Problem
In many enterprises, certificates are issued, deployed, and managed by different groups using different platforms:
• The PKI team owns the internal CA.
• The networking team handles load balancers and web gateways.
• The cloud team spins up short-lived certificates in AWS, Azure, or GCP.
• The DevOps team bakes certs into CI/CD pipelines.
Each team might have its own automation scripts, templates, or vendor tools. None of those systems necessarily talk to each other. That’s how you end up with “islands” of automation — efficient within their scope, but blind to what’s happening elsewhere.
Why Siloed Automation is Risky
The survey shows the most commonly automated processes are workflows and approvals (55%), alerts and notifications (55%), and discovery and inventory (53%). These are often scoped to the systems the PKI team directly controls. That’s a great start, but it leaves huge swaths of the environment — especially cloud and DevOps pipelines — outside the automation perimeter.
Without integration into those other domains, automation can only go so far. And the more fragmented the tooling, the harder it is to expand coverage.
Bridging the Gaps
If you’re trying to make automation work across silos, here’s what I’ve seen work:
1. Inventory Across All Domains
Use discovery tools that reach into on-prem, cloud, and containerized environments. Certificates don’t care about your org chart — neither should your inventory.
2. Standardize Policies Before Tools
Agree on key parameters (validity periods, algorithms, approval workflows) across teams before you try to connect platforms. Without policy alignment, integration just amplifies inconsistencies.
3. Integrate Through Orchestration, Not Just APIs
Point-to-point integrations work for small environments, but orchestration layers scale better. They allow you to push consistent automation policies across multiple systems and CAs.
4. Bring the Right Stakeholders to the Table
Cloud, DevOps, networking, and PKI teams need to design automation together. If you roll out automation that works for one but breaks workflows for another, adoption will stall.
5. Plan for Growth
Certificates are proliferating; everything needs a certificate. This is especially so with the rise of IoT and ephemeral workloads. Whatever integration you build today should be flexible enough to absorb new systems tomorrow.
Case in Point
Here’s an example of one of our customers doing “the right thing” with regards to certificate automation, yet still experiencing issues.
One of our larger public sector customers was managing (at the time) ~65,000 certificates across a mixture of on-prem, cloud first, and hybrid environments between the various business units. The silos had “organically grown” between various business units (networking, business applications, user devices, etc.), yet all were doing “the right thing” in terms of using automation and adopting cloud based approaches.
The Incident
Finally, the inevitable occurred, and there was a major incident. A large number of business users couldn’t remote work effectively.
Some had issues preventing connectivity while others were connecting but unable to reach the business apps they needed. Was it an expired cert(s)? Was it a CRL expiry? A combination of both? Has a change caused “our automation to break down somewhere”? No one had a clear overall view of the business's PKI landscape, and it was a challenge to pinpoint where the issues were occurring.
The Fix
The long term fix came from rolling out an enterprise grade CLM solution. It provided that visibility across business silos to manage the automation. Through discovery and orchestration, they endeavoured to make sure no certificate was missed again.
The Outcome
The outcome was and remains a positive one. There were zero similar outages reported in the following 3+ years. They were able to streamline each silo’s automation processes to provide business improvements when managing certificate changes.
If this can happen to an organization already “doing the right things,” it shows just how urgent coordinated certificate automation really is.
Why Now
Siloed automation might have been “good enough” when certificate lifespans were longer and the attack surface smaller. But with increase in certificate demand, shortening of certificate validity periods, every gap becomes a potential liability. Post-quantum migration will multiply that pressure, requiring thoroughly planned, coordinated changes across all systems that use certificates currently based on classic cryptography. The enterprise move to PQC based certificates is no small task.
Without coordinated certificate automation and integration, those changes will be chaotic at best — and operationally impossible at worst.
Next Steps
To break down silos and unify automation:
• Start with a holistic inventory that covers every certificate in the environment.
• Build a cross-functional automation task force to define policies and priorities.
• Choose tools or orchestration platforms that can span multiple CAs, environments, and use cases.
• Measure and report automation coverage regularly so stakeholders can see progress.
Unifying automation isn’t only about eliminating risk — it’s about creating the operational agility to handle whatever comes next.

About the Author
Todd is the Founder & Chief Technology Officer at Unsung Limited, a company providing "All Things PKI" across different sectors. Todd has over 20 years experience in the Public Key Infrastructure field.


